- Release Notes
- Introduction to CelerData Cloud Serverless
- Quick Start
- Sign up for CelerData Cloud Serverless
- A quick tour of the console
- Connect to CelerData Cloud Serverless
- Create an IAM integration
- Create and assign a warehouse
- Create an external catalog
- Load data from cloud storage
- Load data from Apache Kafka/Confluent Cloud
- Try your first query
- Invite new users
- Design data access control policy
- Warehouses
- Catalog, database, table, view, and MV
- Overview of database objects
- Catalog
- Table types
- Asynchronous materialized views
- Data Loading
- Data access control
- Networking and private connectivity
- Usage and Billing
- Organization and Account
- Integration
- Query Acceleration
- Reference
- AWS IAM policies
- Information Schema
- Overview
- be_bvars
- be_cloud_native_compactions
- be_compactions
- character_sets
- collations
- column_privileges
- columns
- engines
- events
- global_variables
- key_column_usage
- load_tracking_logs
- loads
- materialized_views
- partitions
- pipe_files
- pipes
- referential_constraints
- routines
- schema_privileges
- schemata
- session_variables
- statistics
- table_constraints
- table_privileges
- tables
- tables_config
- task_runs
- tasks
- triggers
- user_privileges
- views
- Data Types
- System Metadatabase
- Keywords
- SQL Statements
- Account Management
- Data Definition
- CREATE TABLE
- ALTER TABLE
- DROP CATALOG
- CREATE TABLE LIKE
- REFRESH EXTERNAL TABLE
- RESTORE
- SET CATALOG
- DROP TABLE
- RECOVER
- USE
- CREATE MATERIALIZED VIEW
- DROP DATABASE
- ALTER MATERIALIZED VIEW
- DROP REPOSITORY
- CANCEL RESTORE
- DROP INDEX
- DROP MATERIALIZED VIEW
- CREATE DATABASE
- CREATE TABLE AS SELECT
- BACKUP
- CANCEL BACKUP
- CREATE REPOSITORY
- CREATE INDEX
- Data Manipulation
- INSERT
- SHOW CREATE DATABASE
- SHOW BACKUP
- SHOW ALTER MATERIALIZED VIEW
- SHOW CATALOGS
- SHOW CREATE MATERIALIZED VIEW
- SELECT
- SHOW ALTER
- SHOW MATERIALIZED VIEW
- RESUME ROUTINE LOAD
- ALTER ROUTINE LOAD
- SHOW TABLES
- STREAM LOAD
- SHOW PARTITIONS
- CANCEL REFRESH MATERIALIZED VIEW
- SHOW CREATE CATALOG
- SHOW ROUTINE LOAD TASK
- SHOW RESTORE
- CREATE ROUTINE LOAD
- STOP ROUTINE LOAD
- SHOW DATABASES
- BROKER LOAD
- SHOW ROUTINE LOAD
- PAUSE ROUTINE LOAD
- SHOW SNAPSHOT
- SHOW CREATE TABLE
- CANCEL LOAD
- REFRESH MATERIALIZED VIEW
- SHOW REPOSITORIES
- SHOW LOAD
- Administration
- DESCRIBE
- SQL Functions
- Function List
- String Functions
- CONCAT
- HEX
- LOWER
- SPLIT
- LPAD
- SUBSTRING
- PARSE_URL
- INSTR
- REPEAT
- LCASE
- REPLACE
- HEX_DECODE_BINARY
- RPAD
- SPLIT_PART
- STRCMP
- SPACE
- CHARACTER_LENGTH
- URL_ENCODE
- APPEND_TAILING_CHAR_IF_ABSENT
- LTRIM
- HEX_DECODE_STRING
- URL_DECODE
- LEFT
- STARTS_WITH
- CONCAT
- GROUP_CONCAT
- STR_TO_MAP
- STRLEFT
- STRRIGHT
- MONEY_FORMAT
- RIGHT
- SUBSTRING_INDEX
- UCASE
- TRIM
- FIND_IN_SET
- RTRIM
- ASCII
- UPPER
- REVERSE
- LENGTH
- UNHEX
- ENDS_WITH
- CHAR_LENGTH
- NULL_OR_EMPTY
- LOCATE
- CHAR
- Predicate Functions
- Map Functions
- Binary Functions
- Geospatial Functions
- Lambda Expression
- Utility Functions
- Bitmap Functions
- BITMAP_SUBSET_LIMIT
- TO_BITMAP
- BITMAP_AGG
- BITMAP_FROM_STRING
- BITMAP_OR
- BITMAP_REMOVE
- BITMAP_AND
- BITMAP_TO_BASE64
- BITMAP_MIN
- BITMAP_CONTAINS
- SUB_BITMAP
- BITMAP_UNION
- BITMAP_COUNT
- BITMAP_UNION_INT
- BITMAP_XOR
- BITMAP_UNION_COUNT
- BITMAP_HAS_ANY
- BITMAP_INTERSECT
- BITMAP_AND_NOT
- BITMAP_TO_STRING
- BITMAP_HASH
- INTERSECT_COUNT
- BITMAP_EMPTY
- BITMAP_MAX
- BASE64_TO_ARRAY
- BITMAP_TO_ARRAY
- Struct Functions
- Aggregate Functions
- RETENTION
- MI
- MULTI_DISTINCT_SUM
- WINDOW_FUNNEL
- STDDEV_SAMP
- GROUPING_ID
- HLL_HASH
- AVG
- HLL_UNION_AGG
- COUNT
- BITMAP
- HLL_EMPTY
- SUM
- MAX_BY
- PERCENTILE_CONT
- COVAR_POP
- PERCENTILE_APPROX
- HLL_RAW_AGG
- STDDEV
- CORR
- COVAR_SAMP
- MIN_BY
- MAX
- VAR_SAMP
- STD
- HLL_UNION
- APPROX_COUNT_DISTINCT
- MULTI_DISTINCT_COUNT
- VARIANCE
- ANY_VALUE
- COUNT_IF
- GROUPING
- PERCENTILE_DISC
- Array Functions
- ARRAY_CUM_SUM
- ARRAY_MAX
- ARRAY_LENGTH
- ARRAY_REMOVE
- UNNEST
- ARRAY_SLICE
- ALL_MATCH
- ARRAY_CONCAT
- ARRAY_SORT
- ARRAY_POSITION
- ARRAY_DIFFERENCE
- ARRAY_CONTAINS
- ARRAY_JOIN
- ARRAY_INTERSECT
- CARDINALITY
- ARRAY_CONTAINS_ALL
- ARRAYS_OVERLAP
- ARRAY_MIN
- ARRAY_MAP
- ELEMENT_AT
- ARRAY_APPEND
- ARRAY_SORTBY
- ARRAY_TO_BITMAP
- ARRAY_GENERATE
- ARRAY_AVG
- ARRAY_FILTER
- ANY_MATCH
- REVERSE
- ARRAY_AGG
- ARRAY_DISTINCT
- ARRAY_SUM
- Condition Functions
- Math Functions
- Date and Time Functions
- DAYNAME
- MINUTE
- FROM_UNIXTIME
- HOUR
- MONTHNAME
- MONTHS_ADD
- ADD_MONTHS
- DATE_SUB
- PREVIOUS_DAY
- TO_TERA_DATA
- MINUTES_SUB
- WEEKS_ADD
- HOURS_DIFF
- UNIX_TIMESTAMP
- DAY
- DATE_SLICE
- DATE
- CURTIME
- SECONDS_SUB
- MONTH
- WEEK
- TO_DATE
- TIMEDIFF
- MONTHS_DIFF
- STR_TO_JODATIME
- WEEK_ISO
- MICROSECONDS_SUB
- TIME_SLICE
- MAKEDATE
- DATE_TRUNC
- JODATIME
- DAYOFWEEK
- YEARS_SUB
- TIMESTAMP_ADD
- HOURS_SUB
- STR2DATE
- TIMESTAMP
- FROM_DAYS
- WEEK_OF_YEAR
- YEAR
- TIMESTAMP_DIFF
- TO_TERA_TIMESTAMP
- DAYOFMONTH
- DAYOFYEAR
- DATE_FORMAT
- MONTHS_SUB
- NEXT_DAY
- MINUTES_DIFF
- DATA_ADD
- MINUTES_ADD
- CURDATE
- DAY_OF_WEEK_ISO
- CURRENt_TIMESTAMP
- STR_TO_DATE
- LAST_DAY
- WEEKS_SUB
- TO_DAYS
- DATEDIFF
- NOW
- TO_ISO8601
- TIME_TO_SEC
- QUARTER
- SECONDS_DIFF
- UTC_TIMESTAMP
- DATA_DIFF
- SECONDS_ADD
- ADDDATE
- WEEKSDIFF
- CONVERT_TZ
- MICROSECONDS_ADD
- SECOND
- YEARS_DIFF
- YEARS_ADD
- HOURS_ADD
- DAYS_SUB
- DAYS_DIFF
- Cryptographic Functions
- Percentile Functions
- Bit Functions
- JSON Functions
- Hash Functions
- Scalar Functions
- Table Functions
Design Data Access Control Policy
Capable of accessing your data lakes as a query engine as well as managing your data within its own database system, CelerData Cloud Serverless provides a complete set of access control strategies that allow you to customize the access control policy for data objects within your account.
This topic describes how to customize a row-level data access control policy for a user.
Prerequisites
You must have and activate the user_admin role to perform this operation.
Understand and activate roles
CelerData Cloud Serverless supports both Identity-based Access Control (IBAC) and Role-based Access Control (RBAC). You can either grant privileges to a role and grant the role to users, or grant privileges directly to users. However, please note that privileges granted through a role only take effect when the role is activated.
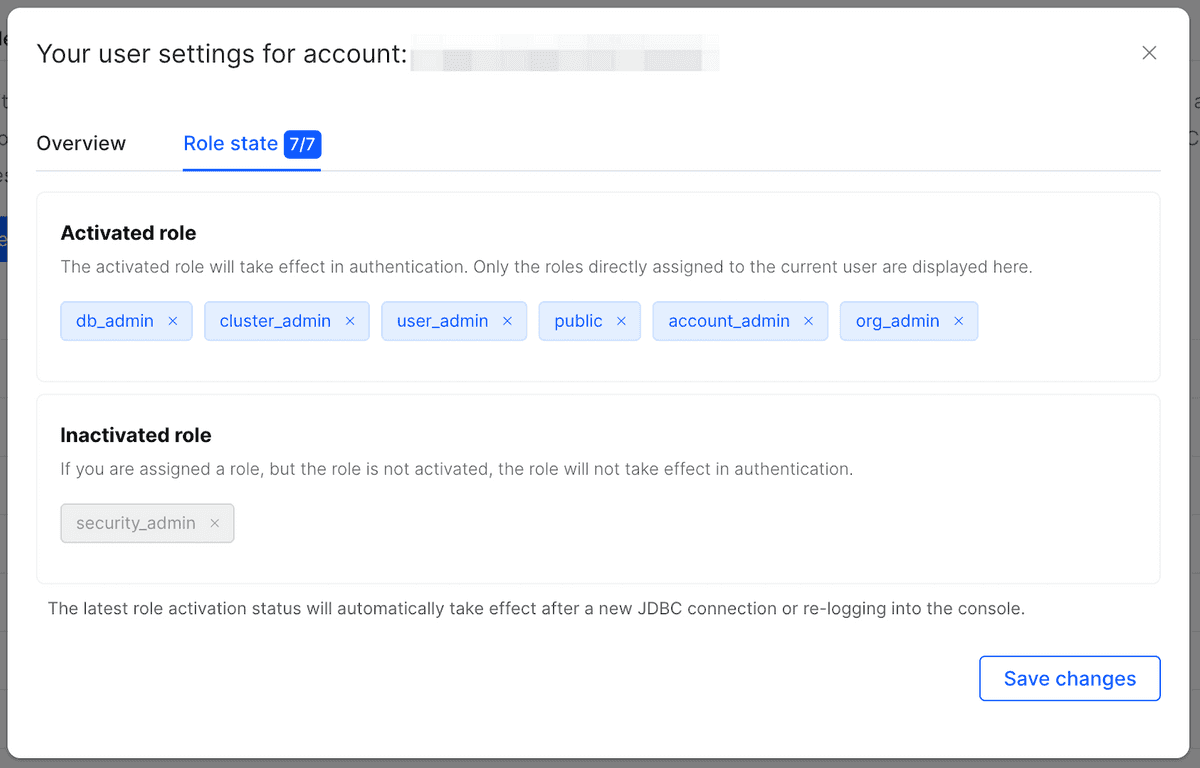
Follow these steps to view the roles granted to you and activate a role from the CelerData Cloud Serverless console:
- Sign in to the CelerData Cloud Serverless console.
- In the upper-right corner of the console, click the user profile icon, and then Activated roles settings.
- On the Role state tab, you can view all roles granted to you, and their activation status.
- Click Modify the role status, activate or deactivate the roles on demand, and click Save changes.
You can also view your roles using SQL commands:
Execute the following SQL statement to view the roles that have been activated for you:
SELECT current_role();Execute the following SQL statement to view all roles that have been directly granted to you:
-- Replace <username> with your username. SELECT FROM_ROLE FROM sys.role_edges WHERE TO_USER = "'<username>'@'%'";
For detailed instructions on managing roles and user privileges, see Manage user privileges.
Grant the read-only privileges of a table to a user
Sign in to the CelerData Cloud Serverless console.
In the left-side navigation pane, choose User&Role.
On the Role tab of the User&Role page, click Create role.
In the Create a new role dialog box, configure the following information and click Create:
- Role name: Enter a name for the role.
- Description: Optionally enter a description for the role.
On the Role tab of the User&Role page, click the role you just created.
On the Granted privileges tab, click Grant new privileges.
In the dialog box that appears, configure the following information, and click Grant:
- Select External catalog or Internal catalog as the type (depending on where the table is stored).
- From the Choose catalog drop-down list, choose the name of the catalog where the table is stored.
- From the Choose privileges drop-down list, choose USAGE.
NOTE
You can grant privileges on the following objects:
- External catalogs
- Internal catalog (
default_catalog) - Databases
- Tables
- Views (only supported in
default_catalog) - Materialized views (only supported in
default_catalog) - Warehouses
On the Granted privileges tab, click Grant new privileges again.
In the dialog box that appears, configure the following information, and click Grant:
- Select Table as the type.
- From the Choose catalog drop-down list, choose the name of the catalog where the table is stored.
- From the Choose database drop-down list, choose the name of the database where the table is stored.
- From the Choose the target table drop-down list, choose the name of the table.
- From the Choose privileges drop-down list, choose SELECT.
Navigate to the User tab of the User&Role page, and click the user to whom you want to grant the privilege.
On the Granted roles tab, click Grant new role.
In the dialog box that appears, choose the role you want to grant from the drop-down list, and click Submit.
After the role is granted to users, they can activate the role by following the steps specified in Understand and activate roles.
Alternatively, you can grant such privileges using SQL commands.
The following example grants the read-only privileges on the table region in the database test from the default_catalog to the role demo_role, and then grants the role to the user brian.
-- Create the role.
CREATE ROLE demo_role;
-- Grant the USAGE privilege on default_catalog to the role.
GRANT USAGE ON CATALOG default_catalog TO ROLE demo_role;
-- Grant the SELECT privilege of the table to the role.
GRANT SELECT ON TABLE test.region TO ROLE demo_role;
-- Grant the role to the user.
GRANT demo_role TO USER brian;
-- Optionally, you can set the role as the default role of the user.
-- Default roles are activated by default.
SET DEFAULT ROLE demo_role TO brian;Set row access policy for a table
CelerData Cloud Serverless supports row-level access control policies.
The following example creates a row access policy that allows demo_role to query only data rows where the column region_value has the value EUROPE.
CREATE ROW ACCESS POLICY regional_policy AS (region_value varchar)
RETURNS boolean ->
CASE WHEN current_role()='demo_role' and region_value='EUROPE' THEN true
WHEN current_role() != 'demo_role' THEN true
ELSE false
END;After the policy is created, you can apply it to the table.
ALTER TABLE test.region ADD ROW ACCESS POLICY regional_policy ON (r_name);With this policy, users with the role demo_role are only allowed to access the data where the region_value is EUROPE in the table region.
For more information about the row access control policies, see Row access control.
Set column masking policy for a table
In addition to granting data access on the row level, CelerData Cloud Serverless also supports restricting users' data access to certain columns of a table using masking policies.
For more information about the column masking policies, see Masking policies.