Create a VPC Network, a Subnet, and Firewall Rules
To deploy a CelerData cluster on GCP, you must specify a subnet for the virtual machine instances on which the cluster depends, and create specific firewall rules for ingress and egress to define the inbound and outbound traffic rules that the cluster nodes must adhere to for cross-node communication and external communication.
- The subnet you use for cluster deployment must reside in the same region where the cluster is deployed.
- If you want to enable Shared VPC for the cluster, you need to follow the instructions provided in Set up Shared VPC to set up a Shared VPC. The VPC network, subnet, firewall rules, Routes, and Public Cloud NAT (or reserved internal static IPv4 address) you used for deployment must belong to the host project of the Shared VPC.
(Optional) Create a VPC network
A subnet must be created under a VPC network. You can follow this section if you do not have a VPC network.
Follow these steps to create a VPC network:
-
Sign in to your project in the Google Cloud console.
-
Expand the left-side navigation menu, and choose VPC Network > VPC networks.
-
Click CREATE VPC NETWORK.
-
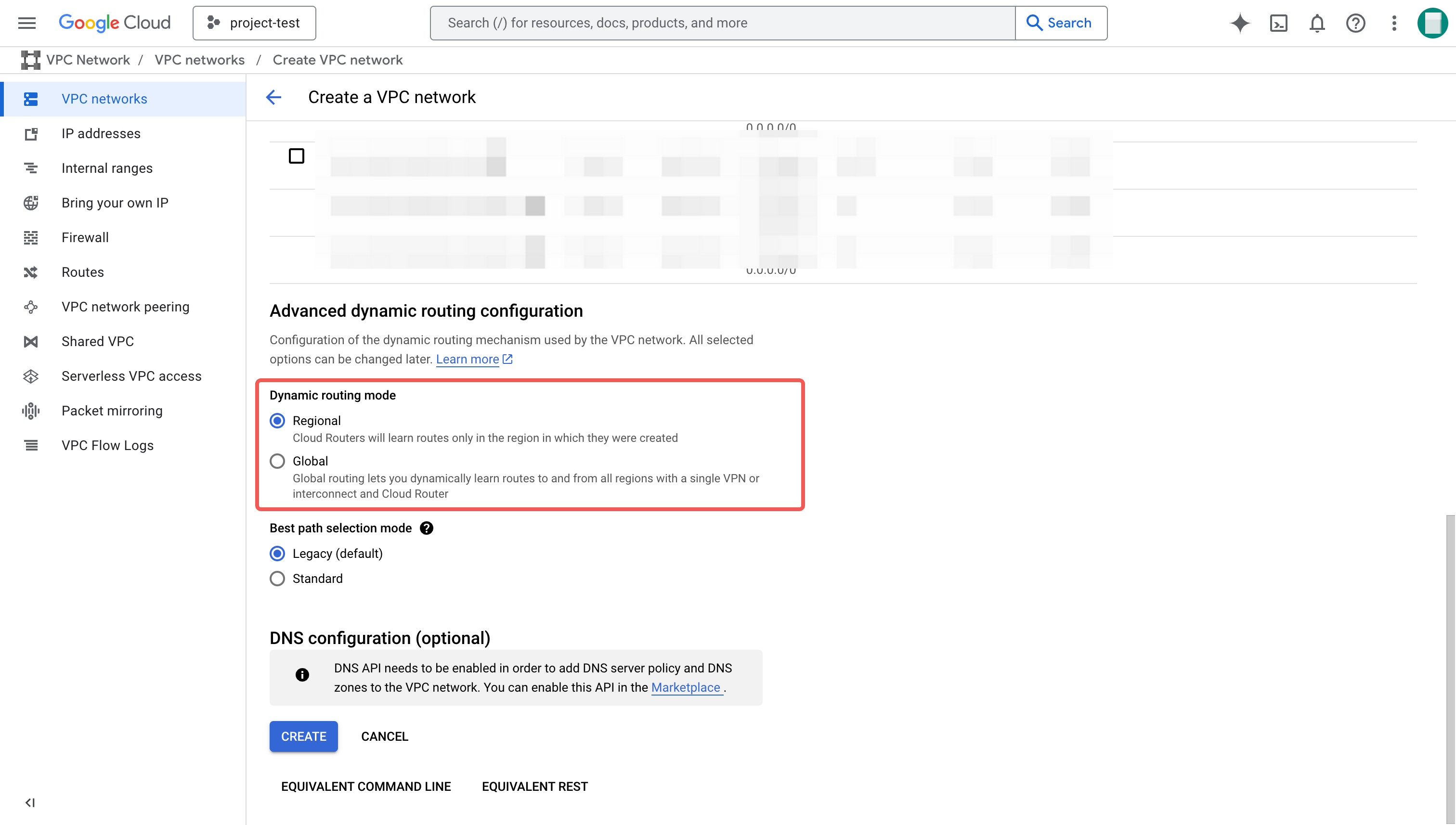
On the Create a VPC network page, follow these steps:
a. Enter the name (for example,
vpc-network-test), and optionally a description for the VPC network.b. Click the Delete button on the New subnet box to skip the step to create a new subnet in this process. You can create it by following the instructions provided in create a subnet after the VPC network is created.
c. For Dynamic routing mode, select Regional.
-
Click Create.
Create a subnet
Follow these steps to create a subnet if did not create one in the previous step:
-
Sign in to your project in the Google Cloud console.
-
Expand the left-side navigation menu, and choose VPC Network > VPC networks.
-
On the VPC networks page, click the VPC network you created in the previous step.
-
On the SUBNETS tab of the VPC network details page, click ADD SUBNET.
-
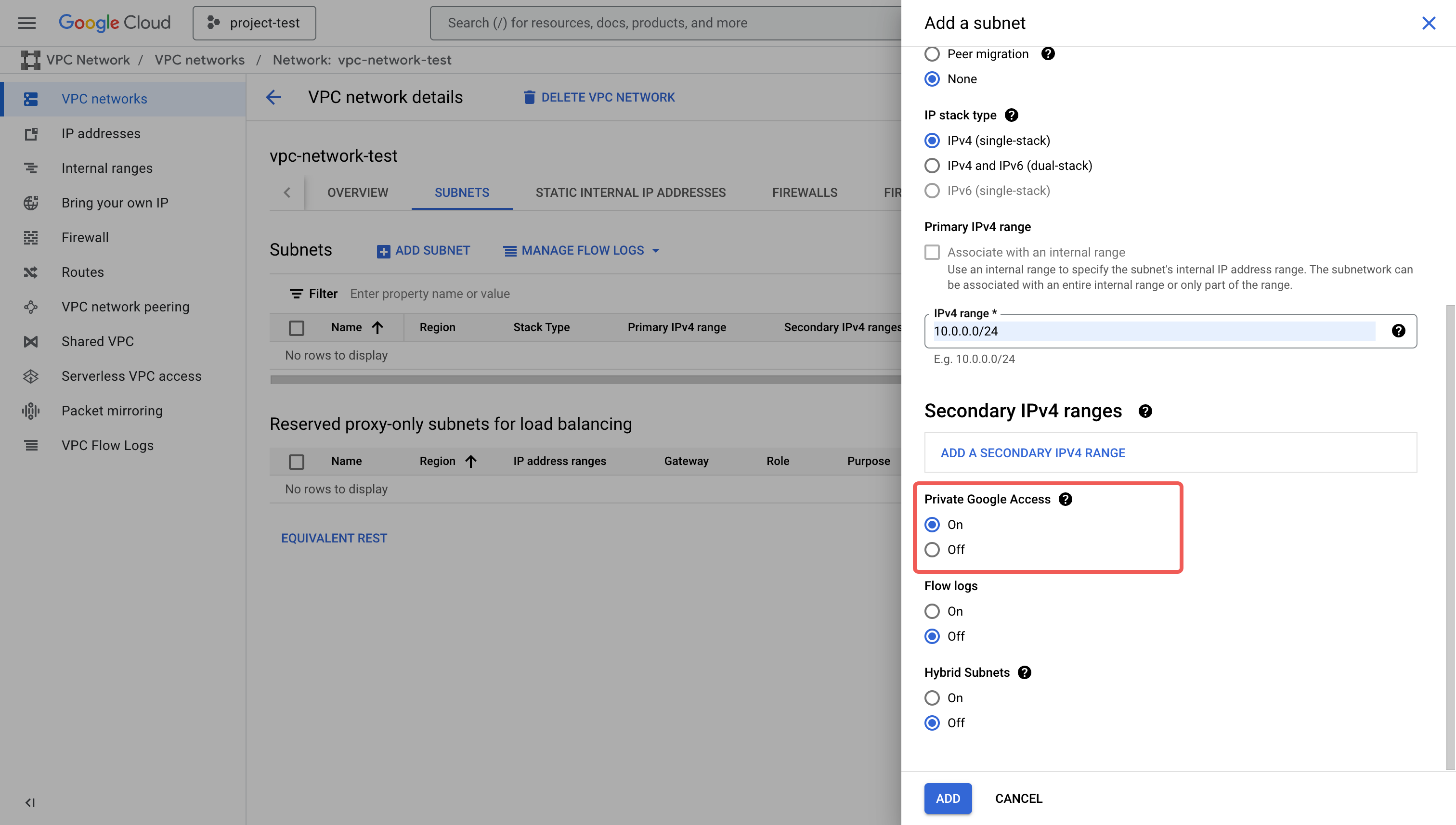
On the Add a subnet tab, follow these steps:
a. Enter the name (for example,
subnet-test) and optionally a description for the subnet.b. For Region, select the region where you want to deploy your CelerData cluster.
c. In the IPv4 range field, specify a CIDR block with at least 255 available IP addresses, for example,
10.0.0.0/24.d. For Private Google Access, select On.
-
Click ADD.
Create firewall rules
You need to create firewall rules for internal ingress and internal egress. If you do not want to use Private Service Connect for secure communication, then you need to create an egress firewall for external communication. It is also recommended to create a firewall rule for NLB health check.
Create an ingress firewall rule for internal communications
Follow these steps:
-
Sign in to your project in the Google Cloud console.
-
Expand the left-side navigation menu, and choose VPC Network > VPC networks.
-
On the VPC networks page, click the VPC network you created in the previous step.
-
On the FIREWALLS tab of the VPC network details page, click ADD FIREWALL RULE.
-
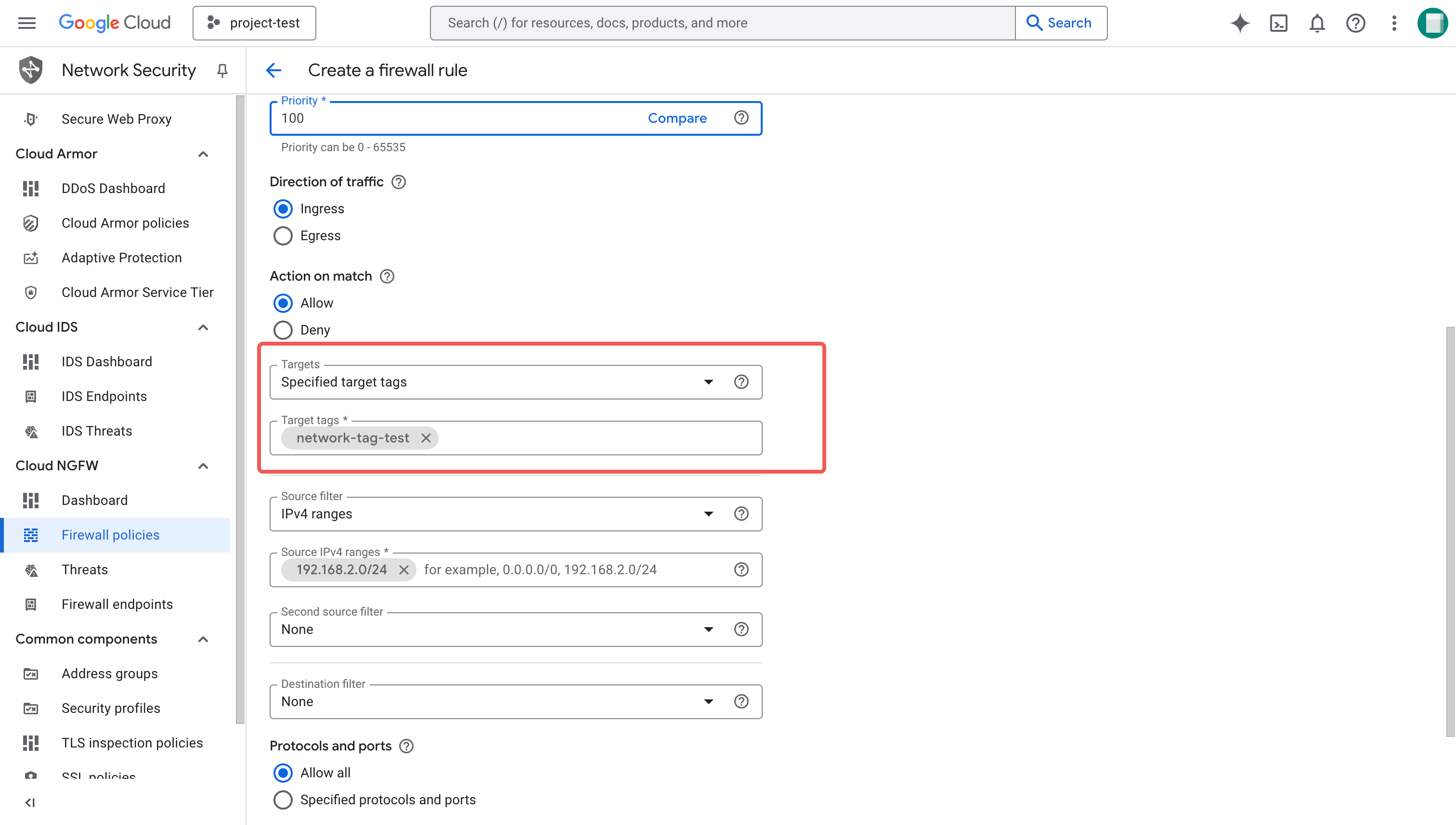
On the Create a firewall rule page, follow these steps:
a. Enter the name (for example,
fr-ingress-internal), and optionally a description for the firewall rule.b. For Network, select the VPC network you created in the previous step.
c. For Direction of traffic, select Ingress.
d. For Targets, select Specified target tags.
e. In the Target tags field, specify a unified tag for all firewall rules to be created for CelerData deployment. This tag will be attached to all virtual machine instances in the cluster deployed under the VPC network.
NOTE
You must specify exactly the same tag in this field. Otherwise, the deployment workflow may fail.
f. For Source filter, select IPv4 ranges.
g. In the Source IPv4 ranges field, specify the CIDR block of the subnet IPv4 range that you set for your subnet. This way, every VM instance (with the target tag) in this subnet can accept traffic from all the sources within this subnet (specified with the CIDR).
h. For Protocol and ports, select Allow all.
-
Click Create.
Create an egress firewall rule for internal communications
Follow these steps:
-
Sign in to your project in the Google Cloud console.
-
Expand the left-side navigation menu, and choose VPC Network > VPC networks.
-
On the VPC networks page, click the VPC network you created in the previous step.
-
On the FIREWALLS tab of the VPC network details page, click ADD FIREWALL RULE.
-
On the Create a firewall rule page, follow these steps:
a. Enter the name (for example,
fr-egress-internal), and optionally a description for the firewall rule.b. For Network, select the VPC network you created in the previous step.
c. For Direction of traffic, select Egress.
d. For Targets, select Specified target tags.
e. In the Target tags field, specify a unified tag for all firewall rules to be created for CelerData deployment. This tag will be attached to all virtual machine instances in the cluster deployed under the VPC network.
NOTE
You must specify exactly the same tag in this field. Otherwise, the deployment workflow may fail.
f. For Destination filter, select IPv4 ranges.
g. In the Destination IPv4 ranges field, specify the CIDR block of the subnet IPv4 range that you set for your subnet. This way, every VM instance (with the target tag) in this subnet can send traffic to all the destination VM instances within this subnet (specified with the CIDR).
h. For Protocol and ports, select Allow all.
-
Click Create.
Create an egress firewall rule for public communications
If you want to use Private Service Connect for secure communication, then you do not need to create this egress firewall rule but to create a PSC Endpoint. Otherwise, you MUST create this external egress Firewall rule to enable the communication between your CelerData cluster and CelerData BYOC Cloud service.
Follow these steps:
-
Sign in to your project in the Google Cloud console.
-
Expand the left-side navigation menu, and choose VPC Network > VPC networks.
-
On the VPC networks page, click the VPC network you created in the previous step.
-
On the FIREWALLS tab of the VPC network details page, click ADD FIREWALL RULE.
-
On the Create a firewall rule page, follow these steps:
a. Enter the name (for example,
fr-egress-external), and optionally a description for the firewall rule.b. For Network, select the VPC network you created in the previous step.
c. For Direction of traffic, select Egress.
d. For Targets, select Specified target tags.
e. In the Target tags field, specify a unified tag for all firewall rules to be created for CelerData deployment. This tag will be attached to all virtual machine instances in the cluster deployed under the VPC network.
NOTE
You must specify exactly the same tag in this field. Otherwise, the deployment workflow may fail.
f. For Destination filter, select IPv4 ranges.
g. In the Destination IPv4 ranges field, specify
0.0.0.0/0, that is, to allow the egress traffic to CelerData BYOC Cloud service.h. For Protocol and ports, select Specified protocols and ports, select TCP, and enter
443in the Ports field under TCP. -
Click Create.
(Optional) Create an ingress firewall rule for public communications
If you want to connect your client applications on a public network to your CelerData cluster or use Stream Load to load data from your local file system, you need to create an ingress firewall rule that allows access to the FE nodes over TCP on ports 9030 and 443 from all IP addresses.
Follow these steps:
-
Sign in to your project in the Google Cloud console.
-
Expand the left-side navigation menu, and choose VPC Network > VPC networks.
-
On the VPC networks page, click the VPC network you created in the previous step.
-
On the FIREWALLS tab of the VPC network details page, click ADD FIREWALL RULE.
-
On the Create a firewall rule page, follow these steps:
a. Enter the name (for example,
fr-ingress-external), and optionally a description for the firewall rule.b. For Network, select the VPC network you created in the previous step.
c. For Direction of traffic, select Ingress.
d. For Targets, select All instances in the network.
e. For Source filter, select IPv4 ranges.
f. For Source IPv4 ranges field:
- If you want to expose your cluster to all applications on public networks, specify
0.0.0.0/0. - If you want to expose your cluster to a specific application on public networks, you can specify the IP addresses of your application.
g. For Protocol and ports, select Specified protocols and ports, select TCP, and enter
443,9030in the Ports field under TCP. - If you want to expose your cluster to all applications on public networks, specify
-
Click Create.
Create an ingress firewall rule for NLB health check
Clients access the CelerData cluster through a Network Load Balancer (NLB) to send SQL queries or submit Stream Load jobs. The NLB performs health checks to monitor the status of FE or Coordinator nodes.
To ensure successful health checks, you need to create an ingress firewall rule that allows access to the FE nodes over TCP on ports 9030 and 443. For more details, see How health checks work.
Follow these steps:
-
Sign in to your project in the Google Cloud console.
-
Expand the left-side navigation menu, and choose VPC Network > VPC networks.
-
On the VPC networks page, click the VPC network you created in the previous step.
-
On the FIREWALLS tab of the VPC network details page, click ADD FIREWALL RULE.
-
On the Create a firewall rule page, follow these steps:
a. Enter the name (for example,
fr-ingress-nlb), and optionally a description for the firewall rule.b. For Network, select the VPC network you created in the previous step.
c. For Direction of traffic, select Ingress.
d. For Targets, select Specified target tags.
e. In the Target tags field, specify a unified tag for all firewall rules to be created for CelerData deployment. This tag will be attached to all virtual machine instances in the cluster deployed under the VPC network.
NOTE
You must specify exactly the same tag in this field. Otherwise, the deployment workflow may fail.
f. For Source filter, select IPv4 ranges.
g. In the Source IPv4 ranges field, enter four IP addresses:
35.191.0.0/16,209.85.152.0/22,209.85.204.0/22, and130.211.0.0/22.h. For Protocol and ports, select Specified protocols and ports, select TCP, and enter
443,9030in the Ports field under TCP. -
Click Create.