Create a Service Account for your Compute Engine
CelerData generates a profile for each query during query execution, and stores it in storage for ease of your reference. The profile is generated by the virtual machine instances on which your CelerData cluster is deployed, and is stored in a Cloud Storage bucket. In addition, if you create an Elastic cluster, the data will be stored in this bucket by default.
You can query the data in the referenced bucket after deployment by using this service account. You can authenticate and authorize access using either VM-based authentication or impersonation-based authentication with this service account.
This topic will guide you on how to create a service account in Google Cloud, and grant it the necessary permissions on your Cloud Storage bucket using an IAM role. You will then need to reference the service account in a data credential, either from the Cloud settings page in the CelerData Cloud BYOC console before you create a deployment or as part of the workflow of creating a deployment.
The Cloud Storage bucket must reside in the same Google Cloud region as the CelerData cluster you want to deploy.
(Optional) Create a Cloud Storage bucket
You can skip this section if you already have a bucket for storing query profile for your CelerData cluster.
-
Sign in to your project in the Google Cloud console.
-
Expand the left-side navigation menu, and choose Cloud Storage > Buckets.
-
Click Create.
-
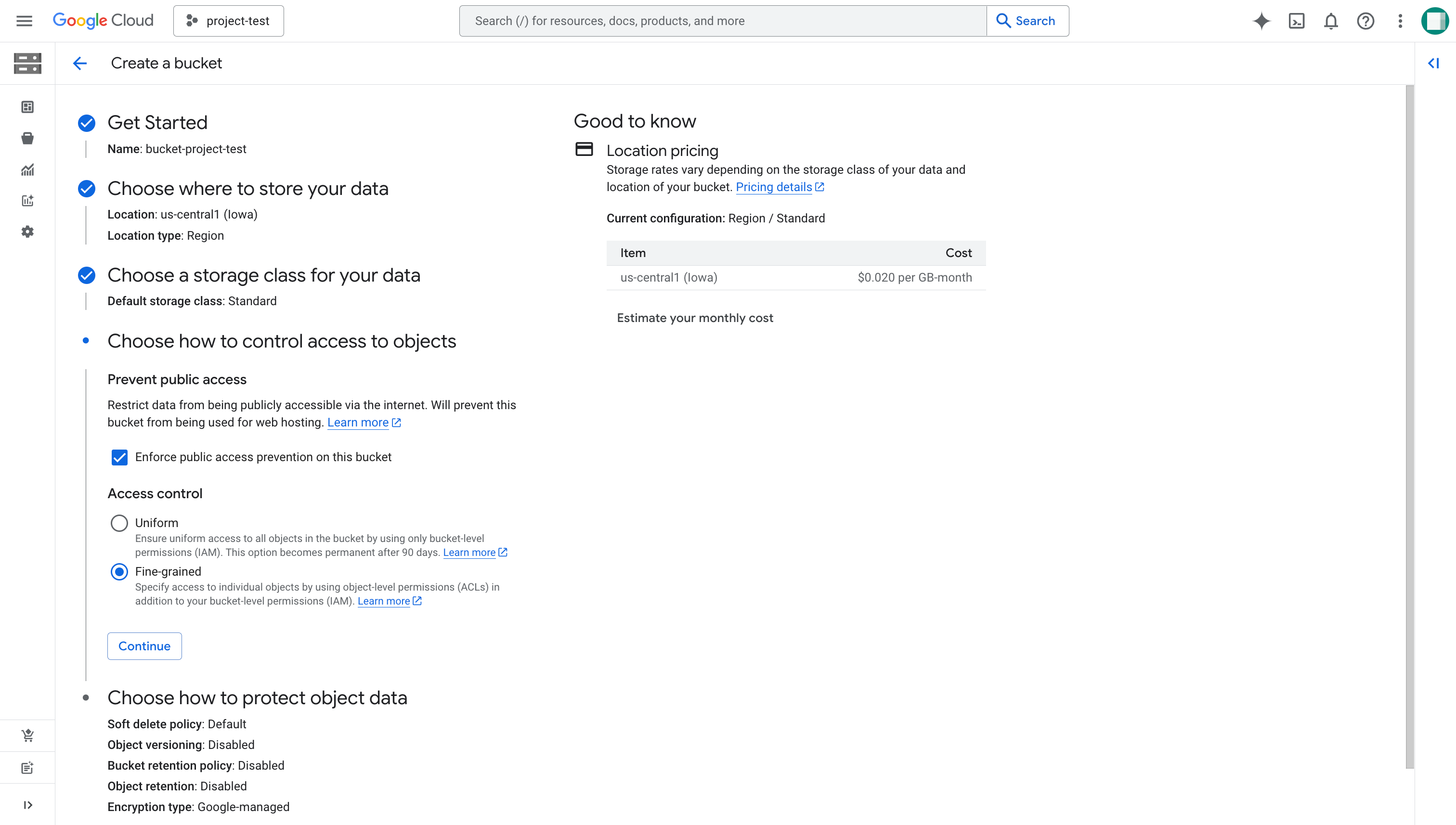
On the Create a bucket page, follow these steps:
a. Enter a globally unique name for your bucket (for example,
bucket-project-test), and click Continue.b. For Location type, choose Region, select the region where you want to deploy your cluster, and click Continue.
c. Choose Set a default Class and then Standard, and click Continue.
d. For Prevent public access, keep Enforce public access prevention on this bucket selected, and select Fine-grained in Access control.
-
Click Create.
Create a service account
Follow these steps to create a service account:
- Sign in to your project in the Google Cloud console.
- Expand the left-side navigation menu, and choose IAM & Admin > Service Accounts.
- Click Create service account.
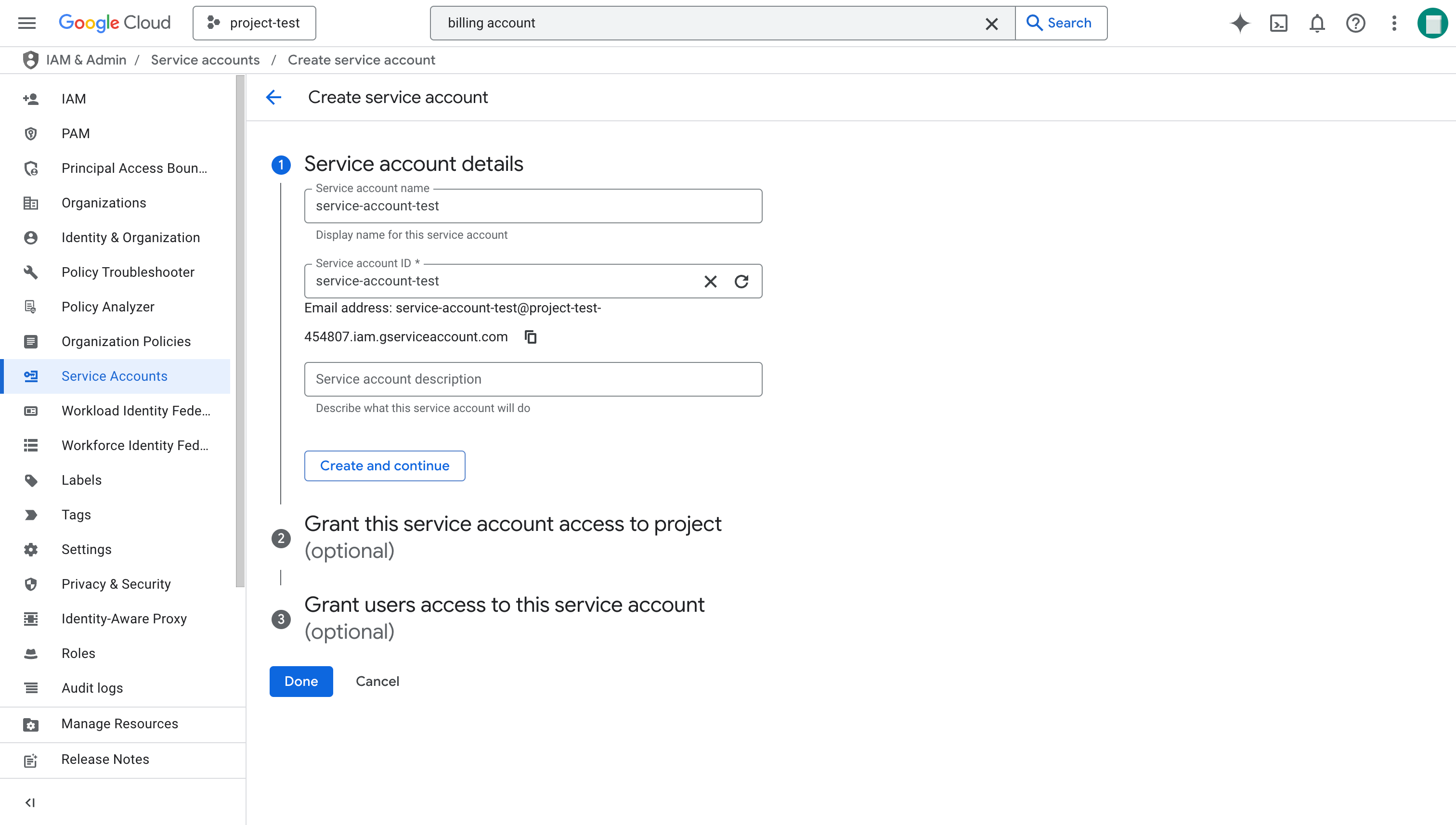
- On the Create service account page, enter the Service account name (for example,
data-service-account), Service account ID (that is the username of the Email address), and optionally a description for the new service account, and click Done.
After the service account is created, copy its Email from the Service Accounts page and save it to a location that you can access later.
Create an IAM role with necessary permissions on the bucket
You need to create an IAM role with the necessitated permissions, and later grant the role to the service account you created in the previous step.
These permissions on your Cloud Storage bucket are required:
iam.serviceAccounts.signBlobstorage.buckets.getstorage.buckets.updatestorage.objects.createstorage.objects.deletestorage.objects.getstorage.objects.liststorage.objects.update
Follow these steps to create the IAM role:
-
Sign in to your project in the Google Cloud console.
-
Expand the left-side navigation menu, and choose IAM & Admin > Roles.
-
Click Create role.
-
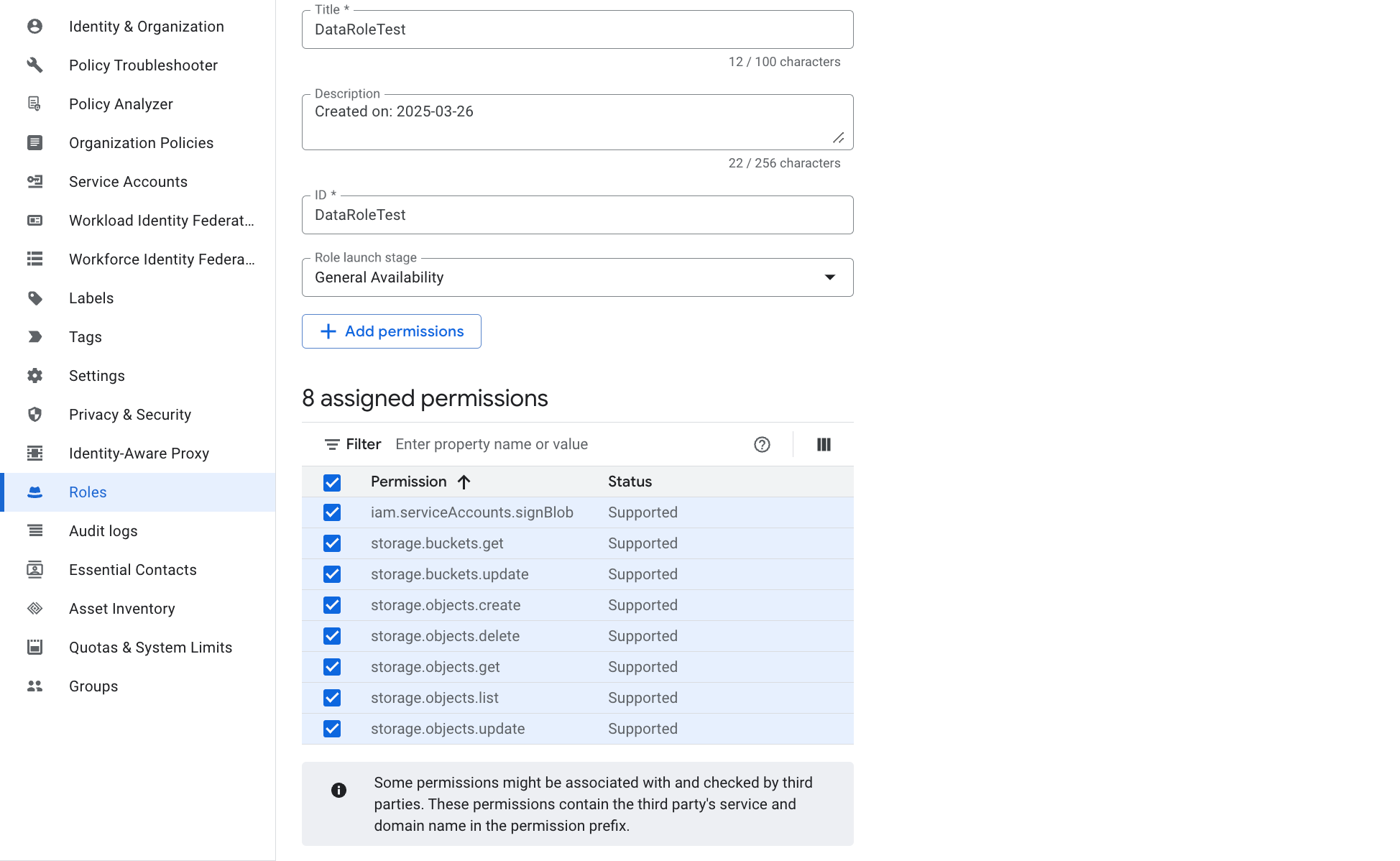
On the Create role page, follow these steps:
a. Enter the title (for example
DataRoleTest), ID, and optionally a description for the new role.b. Select General Availability from the Role launch stage drop-down list.
c. Click Add permissions.
d. On the dialog box that appears, search permission listed above in the Filter, select it, and click Add. Repeat this step until you have added all the permissions listed above.
-
Click Create.
Grant the IAM role to the service account
Follow these steps to grant the IAM role to the service account:
-
Sign in to your project in the Google Cloud console.
-
Expand the left-side navigation menu, and choose IAM & Admin > IAM.
-
On the Allow tab of the IAM page, click Grant access.
-
On the dialog box that appears, follow these steps:
a. Paste the service account Email you copied earlier to the New principals field.
b. Search and select the role you just created (
DataRoleTest) in the Role field.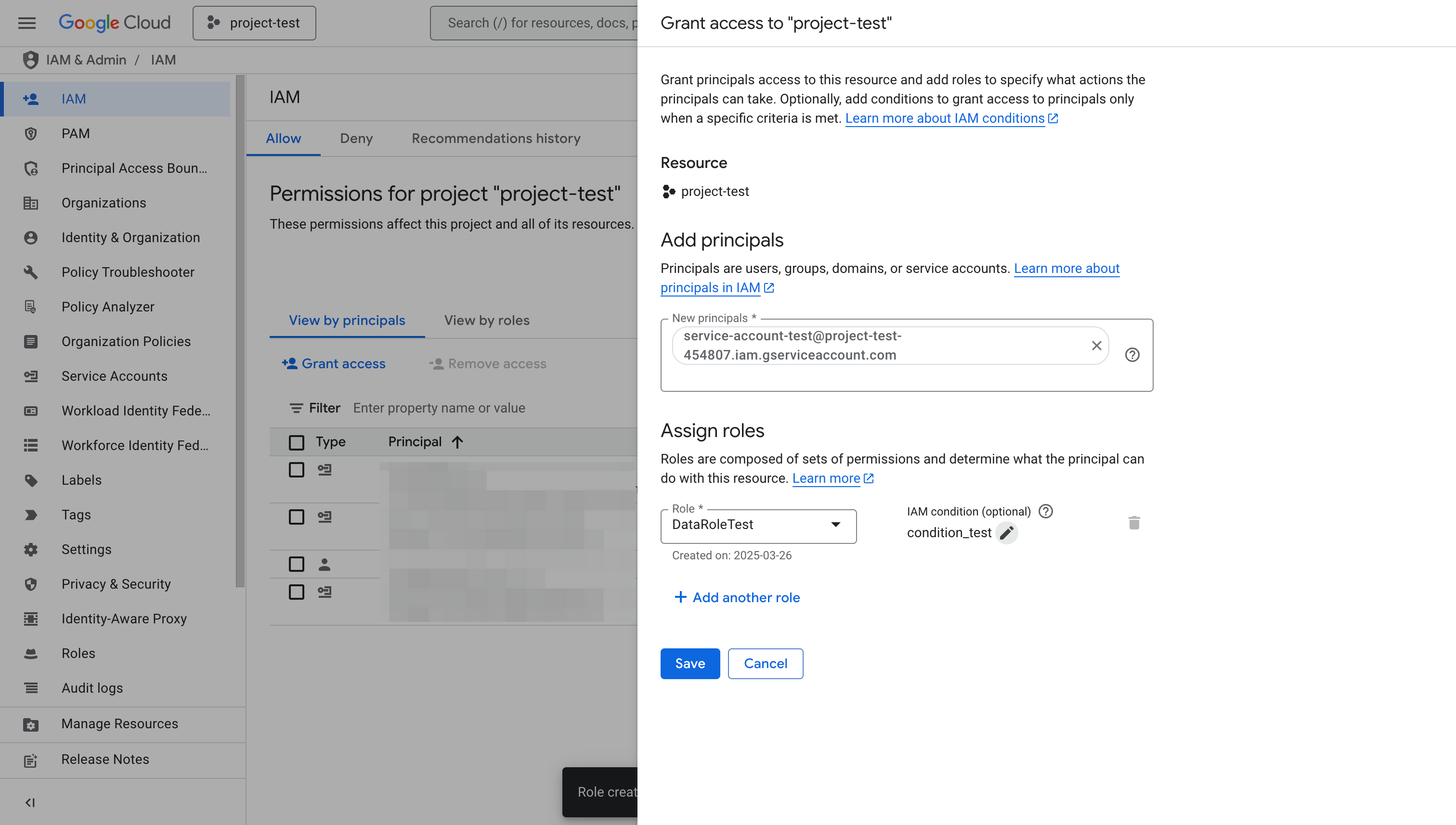
c. Click Add IAM condition.
d. On the new dialog box that appears, enter a title and optionally a description for the condition. On the Condition editor tab, paste the following CEL expression:
resource.name == "" ||
resource.name.startsWith("projects/_/buckets/<bucket_name>/") ||
resource.name == "projects/_/buckets/<bucket_name>"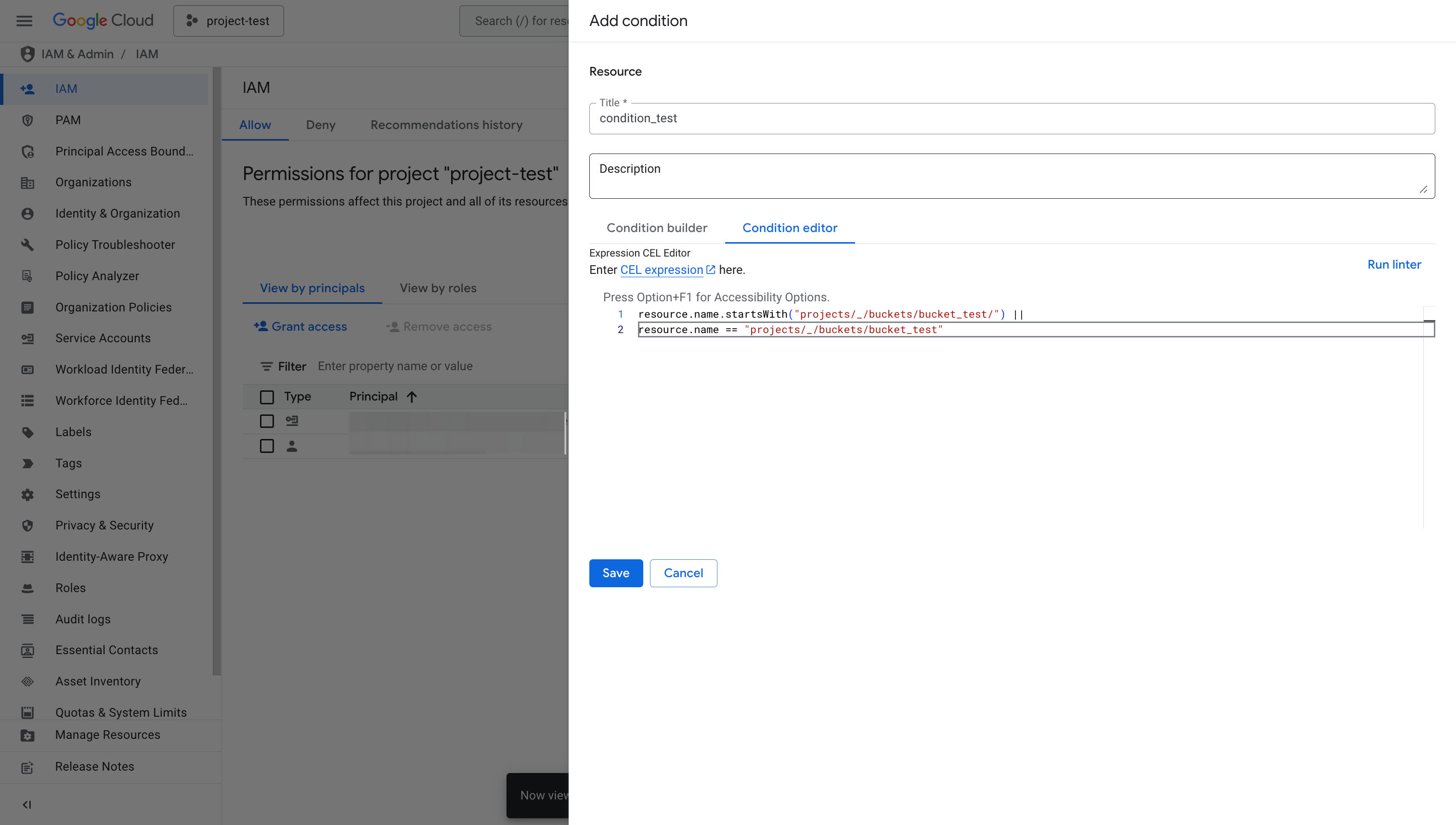 note
noteReplace
<bucket_name>with the name of the Cloud Storage bucket you created for query profile storage in the above CEL expression.e. Click Save to save the condition.
-
Click Save to grant the access.