Security groups and inbound and outbound rules for AWS deployment
This topic provides detailed information of security groups and inbound & outbound rules you may need for your CelerData clusters.
Overview
Usually, you only need to create one security group for your cluster, that is, the Security Group (1) in the following flowchart, or the only security group shown in the End-to-End Private Link solution. This sole security group will control the traffic from and to the cluster, and that between nodes within the cluster. For instructions on creating the sole security group for your CelerData cluster, see Create a security group.
However, if you want to achieve fine-granular security, you can also create dedicated security groups for NLB and VPC endpoint.
The following flowchart illustrates the security groups and inbound & outbound rules you may need in an AWS-based CelerData cluster. For deployment architecture details, see End-to-End Private Link.
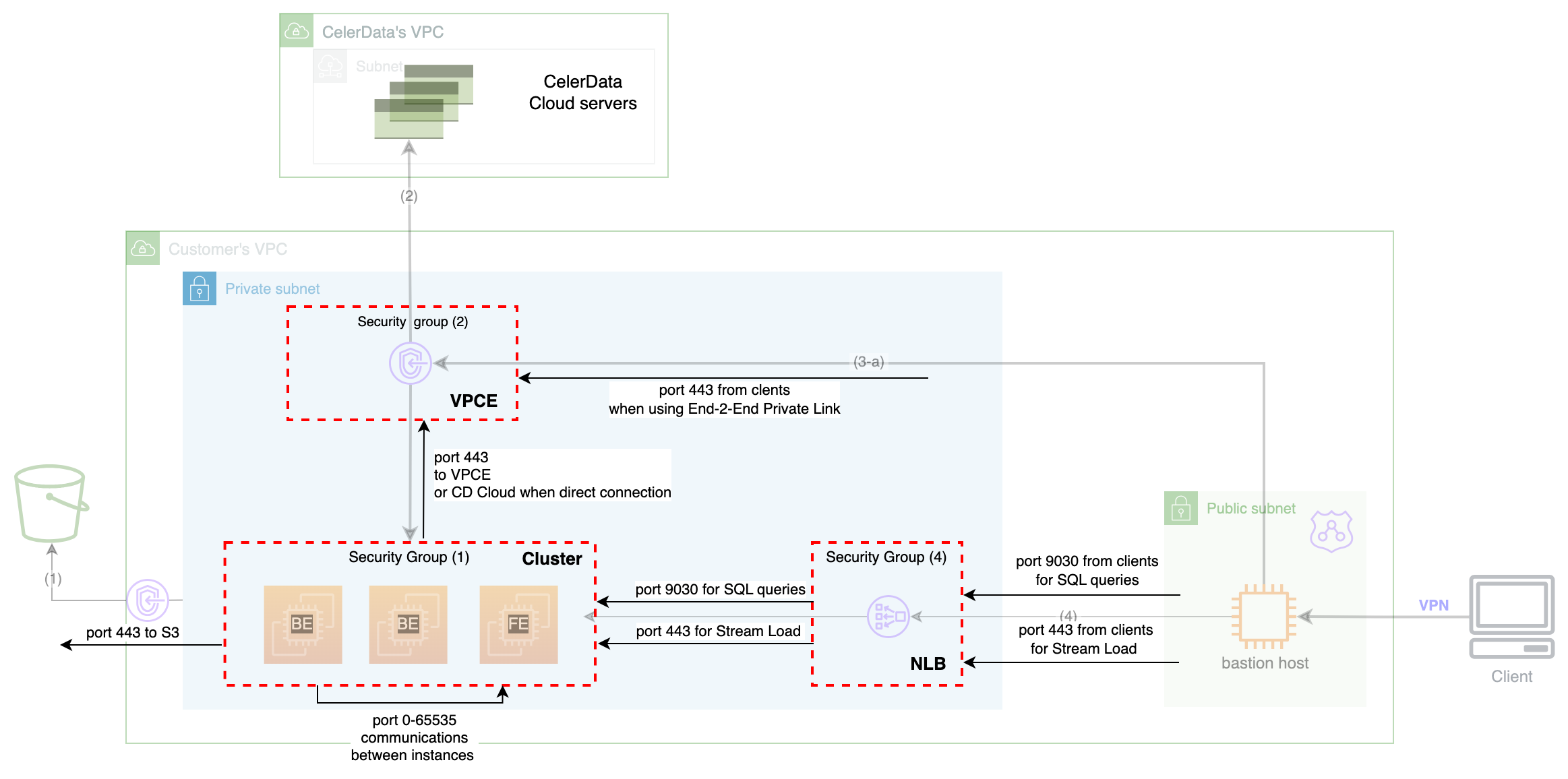
Setting a dedicated security group for NLB
Setting a separate security group for NLB can avoid direct connection to your cluster from clients. As a result, clients can only access the NLB. See Create a security group for NLB for instructions on creating the separate security group for NLB.
If you prefer not to create a separate security group for the NLB, you can omit the inbound and outbound rules between the cluster and the NLB, since they share the same security group (but remember to keep the inbound rules via port 443 and 9030). However, be aware that this allows clients to directly access your cluster via ports 443 and 9030.
Setting a dedicated security group for VPC endpoint
Setting a security group for VPC endpoint can avoid connection to the VPC endpoint from other applications, such as a Flink cluster in the same VPC, which is running only for data processing and does not need to access the VPC endpoint. See Create a VPC endpoint for connection and Create a security group for VPC endpoint for instructions on creating and setting the separate security group for VPC endpoint.
If you choose not to create a separate security group for the VPC endpoint, you can omit the inbound and outbound rules between the cluster and the VPC endpoint, as they use the same security group.
It is also acceptable if you decide not to use a VPC endpoint for a secure connection. In this case, you must add an outbound rule to the cluster's security group that allows traffic to destination 0.0.0.0/0 (CelerData Cloud servers) over port 443.